Watch on YouTube
Introduction
Cross-site request forgery (CSRF) is a cyberattack where a malicious website exploits a user's browser to send unauthorized requests to a legitimate site. This dangerous vulnerability can affect even the largest platforms and were discovered at TikTok, YouTube, and ING Direct. In this blog post, we'll explore how CSRF attacks work and why they're so challenging to detect.
Understanding Browser-Server Interactions
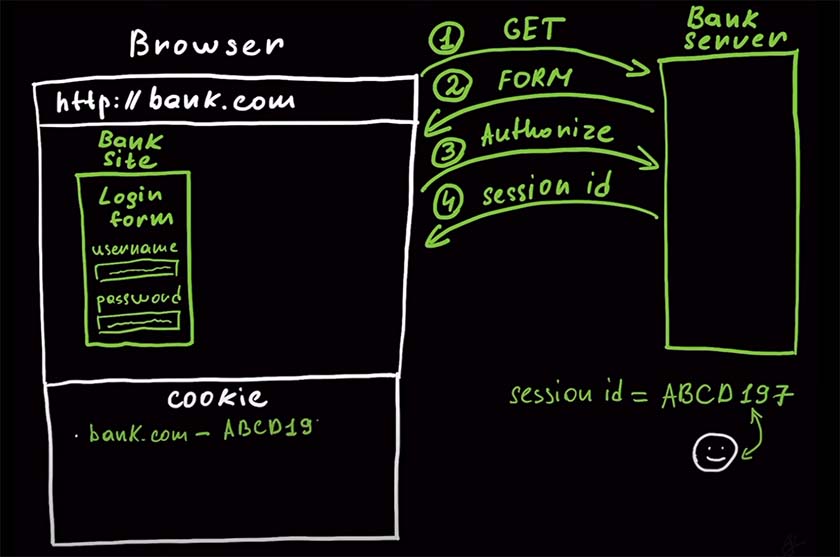
To grasp how CSRF attacks happen, it's essential to understand how browsers and web servers interact. When you enter a URL in your browser, it sends a GET request to the corresponding web server to retrieve the desired webpage. Once you log in to a site with your credentials, the server generates a session ID as a temporary substitute for your login information. This session ID is stored in a browser cookie and is automatically sent with every subsequent request to the web server.
The Mechanism of CSRF Attacks
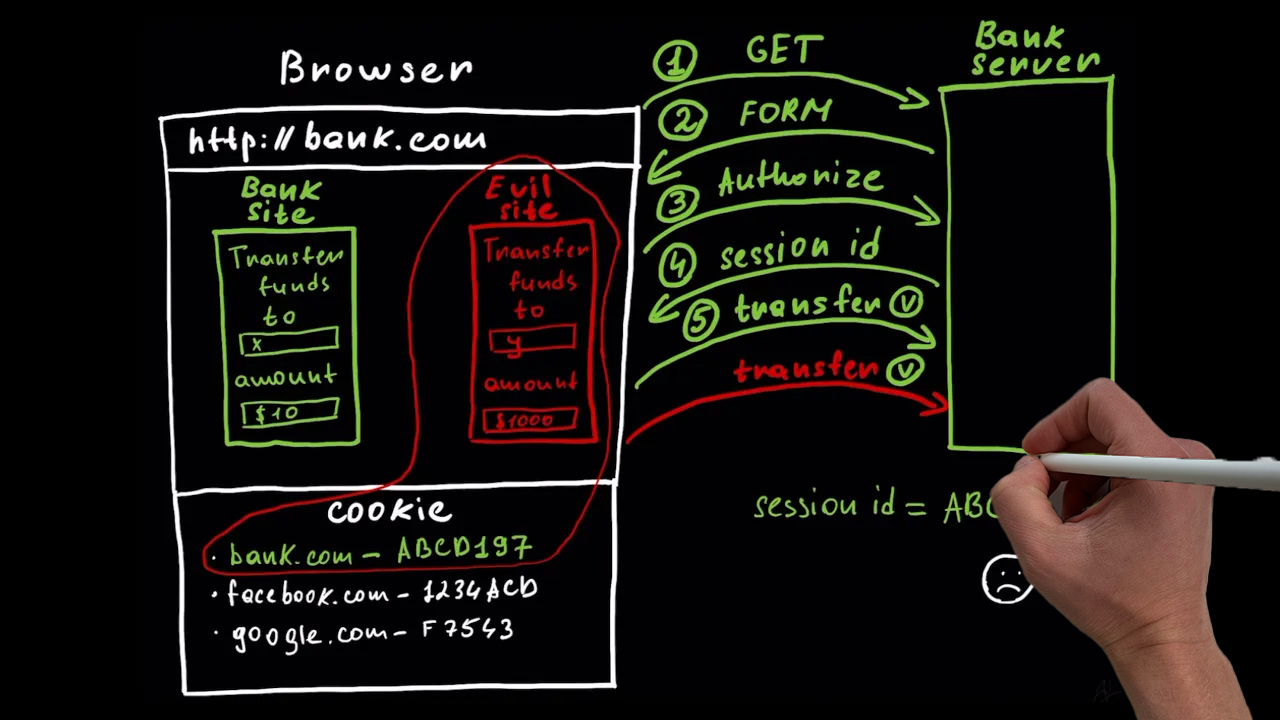
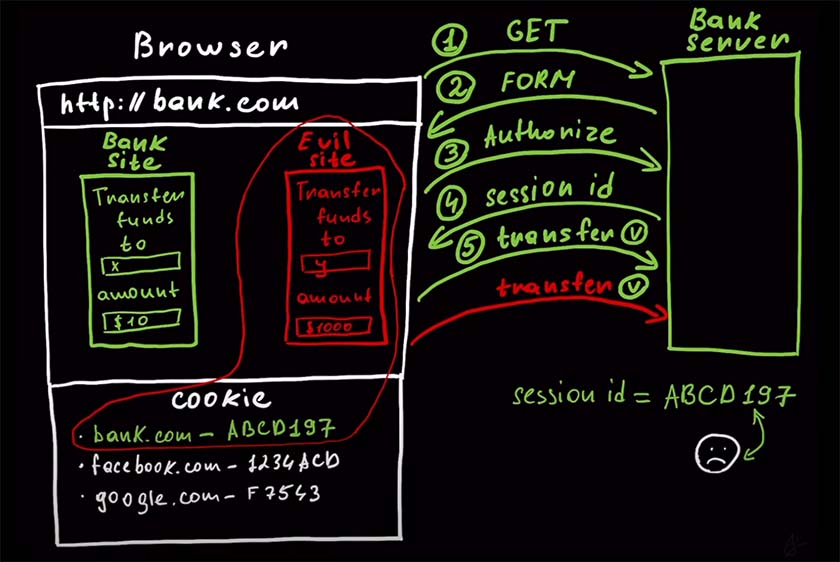
The CSRF attack begins when an attacker creates a malicious website containing code that initiates unauthorized requests, such as transferring funds or changing passwords. This code is often hidden in a form, image, or advertisement, and may closely resemble a genuine form from a legitimate website. When a user clicks a link on the malicious site, the hidden form sends a request to the targeted web server. Because cookies are automatically attached to every request, the session ID is included, and the server can't distinguish between legitimate and malicious requests.
Exploitation of CSRF Vulnerability by Malicious Websites
Malicious websites take advantage of a target site's cookies and the inherent trust placed in session IDs to exploit CSRF vulnerabilities. When a user visits the evil website, it uses the victim's browser to craft a malicious request that appears legitimate to the target site. Since cookies are automatically attached to every request, the session ID cookie of the target site is included in the malicious request. This enables the attacker to bypass authentication checks and perform unauthorized actions, such as transferring funds or changing user passwords. The target site's inability to differentiate between legitimate and malicious requests, combined with the automatic behavior of browsers, creates a perfect environment for CSRF attacks to thrive.
Real-World Examples of CSRF Attacks
Over the years, several high-profile CSRF attacks have occurred:
- In 2020, a vulnerability in TikTok allowed attackers to perform one-click account takeovers by changing user passwords
- In 2008, a CSRF vulnerability on YouTube enabled attackers to send messages, comment on videos, and more on behalf of users
- That same year (2008), Dutch bank ING Direct experienced a CSRF vulnerability that allowed attackers to transfer funds from user accounts.
Defending Against CSRF Attacks
It's crucial to protect websites and users from CSRF attacks. In our next blog post, we'll discuss effective methods to safeguard against these vulnerabilities. Stay tuned to learn how to secure your online presence from CSRF threats.
Conclusion
Cross-site request forgery is a potent cybersecurity threat that exploits the automatic behavior of browsers and the trust placed in session IDs. By understanding how CSRF attacks work and how they can impact users and websites, we can better prepare to defend against these silent and dangerous vulnerabilities.